In response to the Daily Prompt:
How do you manage your online privacy? Are there certain things you won’t post in certain places? Information you’ll never share online? Or do you assume information about you is accessible anyway?
Privacy? What’s that?
In case you haven’t heard, the National Security Agency (NSA) has been spying on us for years. President Truman established the NSA in 1952. Since then, the NSA has continuously overstepped the boundaries of what is considered “legal surveillance.”
As early as 1975, it was noted how dangerous the NSA could be to the American people. A bipartisan Senate investigation stemming from Watergate, led by Sen. Frank Church, found the NSA and other intelligence agencies engaged in a massive domestic spying program, targeting anti-war protesters, civil rights activists, and political opponents. Sen. Church remarked: “That capability at any time could be turned around on the American people, and no American would have any privacy left, such is the capability to monitor everything: telephone conversations, telegrams, it doesn’t matter. There would be no place to hide.”
In December of 2000, the NSA declares it needs a direct access to information. In a report about the NSA’s mission for the 21st Century, the agency notes: “The volumes of routing of data make indexing and processing nuggets of intelligence information more difficult. To perform both its offensive and defensive mission, NSA must “live on the network.”
It wasn’t until “the incident” of September 11, 2001, that things really started to shift. Ex-NSA Analyst J. Kirk Wiebe recalls: “everything changed at the NSA after the attacks on September 11. The prior approach focused on complying with the Foreign Intelligence Surveillance Act (“FISA”). The post-September 11 approach was that NSA could avoid federal statutes and the Constitution as long as there was some visceral connection to looking for terrorists.” While another ex-NSA analyst also remembers: “The individual liberties preserved in the US Constitution were no longer a consideration [at the NSA].”
Then, in October of 2001, good old President Bush signed off on a secret eavesdropping operation so sensitive that even many of the country’s senior national security officials, men and women with highest security clearances in his administration, knew nothing about. This allowed the NSA to spy on four types of data: “1) telephony content, 2) Internet content, 3) telephony metadata, 4) Internet metadata.
There is a lot more detail in a leaked NSA Inspector General report about how this secret eavesdropping operation progressed. Including, how General Mike Hayden began approaching telecommunications companies to voluntarily give the government data. As the report states, “General Hayden stated that the National Security Agency and Federal Bureau of Investigation required their assistance ‘to collect intelligence vital to the national security arising from the events of 11 September 2001,’ and specifically requested that they ‘provide survey, tasking and collection against international traffic, some of which terminates in the United States; provide aggregated call record information; and supply computer to computer data which can be used to determine the communicants.’ Their assistance was ‘needed to identify members of international terrorist cells in the United States and prevent future terrorist attacks against the United States.’ These first letters also stated that the request was authorized by the President with the legal concurrence of the Attorney General, pursuant to Article II of the Constitution.”
Bush’s Law by Eric Lichtblau recalls much of the information from the Mark Klein declaration. Lichtblau writes: AT&T technician Mark Klein “answered the door of his office complex…to find an NSA representative who was there on an undisclosed mission. Not long after Klein learned of a secret room being built on the sixth floor of another AT&T facility on Folsom Street” in San Francisco. “Then he heard from other AT&T technicians about similar mystery rooms in other cities across the country. As Klein pieced together all the strange things he’d seen, the first thing he thought about was George Orwell’s 1984.”
Another thing worth mentioning is how this program was presented to officials, to sign off on, with such an urgency, that most did not even read it. According to 500 Days: Secrets and Lies in the Terror Wars by Kurt Eichenwald. “Ashcroft was informed about [the Program] after Bush had okayed it and was only then asked to attest that the initiative complied with the law. Ashcroft gave his after-the-fact certification of the program’s legality on the same day he learned of it. He conducted no legal research to verify his conclusions.
Now, a lot more has come out since whistleblower Edward Snowden provided hundreds of top-secret NSA documents. PRISM is one NSA operation that uses the help of telecommunications companies. The technology companies, whose cooperation is essential to PRISM operations, include most of the dominant global players of Silicon Valley, according to the documents. They are listed on a roster that bears their logos in order of entry into the program: “Microsoft, Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube, Apple.” PalTalk, although much smaller, has hosted traffic of substantial intelligence interest during the Arab Spring and in the ongoing Syrian civil war. Dropbox, the cloud storage and synchronization service, is described as “coming soon.”
A lot of these companies denied these allegations at first. Then they tip toed around the issue, claiming they were forced to allow the NSA access to their servers. Now, we are supposed to believe that none of this happens anymore? Especially since it’s been disclosed that the NSA has methods to ensure they have control over the setting of international encryption standards. The have the use of supercomputers to break encryption with “brute force.” Since the NSA already had access to these company’s infrastructure, there most probably still are secret vulnerabilities – known as backdoors or trapdoors, in these company’s encryption software.
It’s also been revealed that the NSA implants malware in firmware. Most pieces of hardware on a modern computer are complex enough that they need their own tiny computers in order to operate. Devices such as your hard disk, network card, BIOS, keyboard, USB drives, and video cards all have their own microprocessor, memory, and software—separate from the CPU, RAM, and other components that make up your actual computer. This lower-level software and operating system is called “firmware”. There is firmware in most electronic devices that we use: cellphones, car components, printers, digital cameras, TVs, routers, etc., all contain firmware.
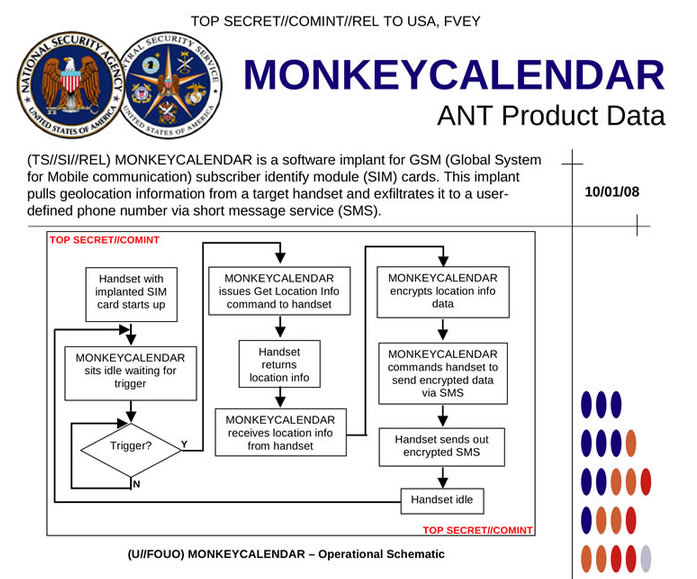 It’s also been suggested that the NSA has implanted malware in the SIM cards of our phones. This allows governmental agencies not only the power to monitor cellular communications, including calls and data, but they also come with additional perks, such as the power of instructing a device to install specific programs. The NSA and GCHQ could use OTA keys — basically keys that let carriers push over-the-air updates to phones. OTA keys provide total access to a phone, and even allow agencies to delete any trace to suspicious OTA updates, making the spyware “completely hidden from the user.”
It’s also been suggested that the NSA has implanted malware in the SIM cards of our phones. This allows governmental agencies not only the power to monitor cellular communications, including calls and data, but they also come with additional perks, such as the power of instructing a device to install specific programs. The NSA and GCHQ could use OTA keys — basically keys that let carriers push over-the-air updates to phones. OTA keys provide total access to a phone, and even allow agencies to delete any trace to suspicious OTA updates, making the spyware “completely hidden from the user.”
And to top it off, the NSA has figured out how to hide spying software deep within hard drives made by Western Digital, Seagate, Toshiba and other top manufacturers, giving the agency the means to eavesdrop on the majority of the world’s computers
There you have it. Is there any privacy? Big Brother Is Watching.






Pingback: 7 Easy Tips On How To Prevent WordPress Hacking | What I Gotta Say About It