Photos have been modified from photos on Wikipedia.
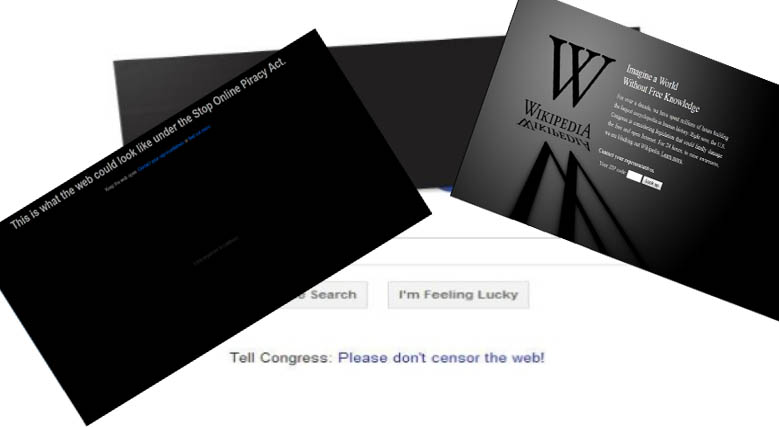
Do you remember seeing web pages being displayed like the ones above? Nearly two years ago, On January 18, 2012, a series of coordinated protests occurred against two proposed laws in the United States Congress—the Stop Online Piracy Act (SOPA) and the PROTECT IP Act (PIPA).
These bills were presented to the government in late 2012 as a way to enforce U.S. laws against websites outside U.S. jurisdiction. It was suggested that it would help combat copyright infringing activities and the sales of counterfeited products by cutting off infringing sites from U.S. based adverting and payment processing. It would also have stopped these sites from appearing on search engines and from having any visibility on web browsers. This would have been done by modifying the entire DNS system, which, by the way, is how computers find each other all around the world. This would have been the first step towards becoming something like the great firewall of China, in where the government and/or invested corporations choose what to allow through.
One of the most instrumental persons who helped to defeat these bills from becoming a reality, was Aaron Swartz.
Aaron Swartz was considered an internet prodigy. According to a movie documenting his life, The Internet’s Own Boy, he had a thirst for knowledge and started developing software at a very young age.
Aaron Swartz fought for an Internet grounded in community, creativity, and human rights. At age 14, Swartz helped create RSS, a method of syndicating content on the Web. He also co-created the Creative Commons and Reddit platforms as well as the technology that became SecureDrop. He helped make information accessible.
As bloggers, most of us use the Creative Commons licenses often. It’s a suite of licenses creators can use to enable sharing, remixing, and collaboration. In fact, Brian Knappenberger has made The Internet’s Own Boy available under a Creative Commons license and can be downloaded and shared for free from the Internet Archive.
It frustrated Aaron that scores of books and journals were increasingly being digitized and locked up by a handful of private corporations. He wanted to make it easier to learn about the laws that we have to live with everyday and make it easy to have access to these academic articles that form the building blocks of our knowledge about the world.
He wrote about the need for open access in the Guerilla Open Access Manifesto and soon afterward started , projects like The Open Library that seeks to make one webpage for every book published (imagine a future where we don’t link to Amazon when directing people to a book). And during his brief stint at Stanford, Aaron worked with a law student to download the entire Westlaw database of law review articles and found troubling connections between funders of research and favorable conclusions.
Aaron went even further with the PACER system. PACER charges per page to view US court documents that are a matter of public record. Encouraged by Carl Malamud, Aaron wrote a computer program that downloaded 20 million pages of federal court documents. In the process, scores of privacy violations were found in the PACER documents, which revealed Social Security numbers, Secret Service agents’ identities, and the like, leading to stricter privacy enforcement in the courts. This made Aaron the target of a FBI investigation that was later dropped. He donated the pages he downloaded to public.resource.org, an open government initiative spearheaded by Carl Malamud.
Aaron’s luck ran out 3 years later when he gained illegal access to JSTOR, a subscription database of academic papers, through MIT’s networks and downloaded millions of documents.
He was originally charged with two state charges of breaking and entering with intent to commit a felony. Afterward, the federal grand jury charged him with wire fraud, computer fraud, unlawfully obtaining information from a protected computer and recklessly damaging a protected computer. Aaron was eventually indicted by a Middlesex County Superior Court grand jury on state charges of breaking and entering with intent, grand larceny and unauthorized access to a computer network. Then, state prosecutors filed a notice that they were dropping the two original charges. According to a spokesperson for the Middlesex County prosecutor, the state charges were dropped to focus on the federal prosecution. On September 12, 2012, federal prosecutors filed a superseding indictment adding nine more felony counts.
JSTOR eventually stopped their pursuit of charges against Aaron for his activities. However, our Federal Government was not so kind. They decided to make an example of Aaron and charged him with multiple felonies. Charges that carried up to 35 years in prison and $1 million in fines. Aaron was found dead in his Brooklyn apartment two years ago on January 11, 2013, in an apparent suicide.
At the time of his death, Aaron was being prosecuted under the Computer Fraud and Abuse Act (CFAA). Many, including Aaron’s family and girlfriend, believed that Aaron’s taking of his own life was related to these charges. Others believe that the charges did not match the crime, and that he was being over-prosecuted. In a statement, the family said his apparent suicide was “the product of a criminal justice system rife with intimidation and prosecutorial overreach.” Alex Stamos, an expert witness in the JSTOR trial, wrote a piece saying that Aaron’s actions did not justify the charges brought against him.
Aaron’s tragedy shines a spotlight on a couple profound flaws of the Computer Fraud and Abuse Act (CFAA) and gives us an opportunity to think about how to address them.
First of all, Hacking laws are too broad, and too vague. Among other things, the CFAA makes it illegal to gain access to protected computers “without authorization” or in a manner that “exceeds authorized access.” But what does a lack of “authorization” actually means. Prosecutors have taken advantage of this confusion to charge people with hacking a computer but in reality it was most likely based on other behaviors the prosecutors didn’t like.
An example of this is United States v. Drew. In this case, a woman created a fake MySpace page to taunt a teenage girl. The girl became distraught and ended up committing suicide. Bullying itself isn’t illegal, so prosecutors charged Drew under the CFAA, claiming her fake profile violated MySpace’s terms of use, which made her access to the social networking site’s computers “unauthorized.”
So, there are many people who are using fake names on web sites. In the fine print of many web services, it is against their terms of use not to put your real name. Many of us intentionally or unintentionally violate those agreements every day. Prosecutors wouldn’t bother filing criminal charges against most of us, of course. But if they wanted to, they would have the leeway to do it under the government’s theory. Are you at risk?
Aaron’s friends and family have worked with lawmakers to find solutions with to this problem. Several people who have worked with Aaron and Demand Progress on SOPA and other issues — are taking action.
Help make sure this never happens to anyone again. Help Fix the law they used to persecute Aaron and demand a Congressional inquiry into his abusive prosecution.
If you’re on Facebook, click here to share with your friends.
If you’re on Twitter, click here to tweet about the campaign.




Pingback: The Guise Of Security | What I Gotta Say About It
Pingback: I Won't Be Provoked Into Self-Censorship | What I Gotta Say About It